In 2019 alone, 65% of U.S. organizations experienced a successful phishing attack (2020 State of the Phish, Proofpoint).
Now let’s look at a few examples!
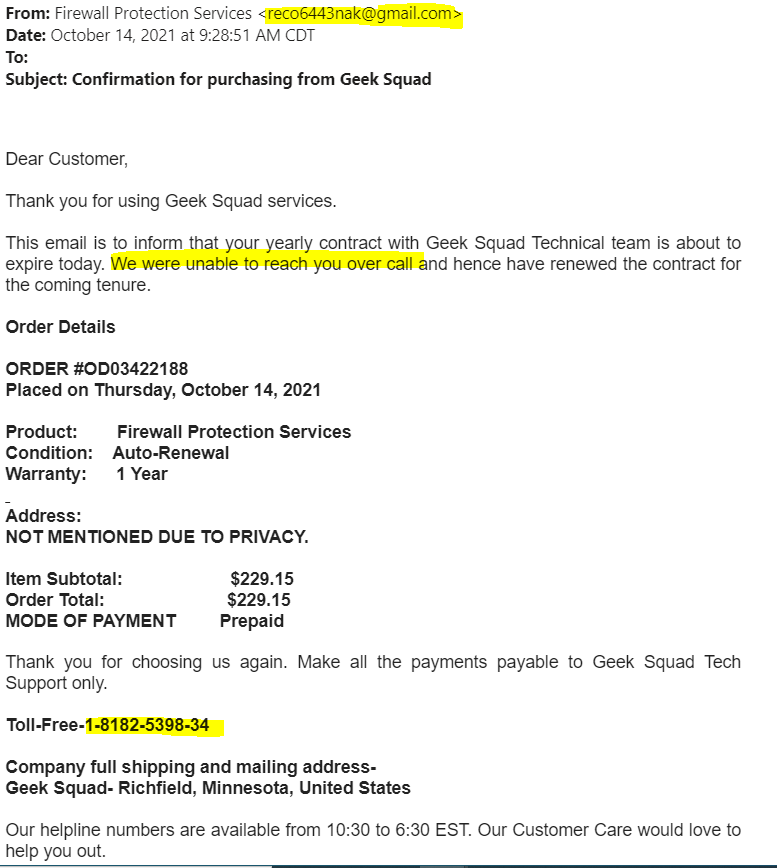
I will start with the top and work my way down the email. Let’s start with the email address that sent the email. Notice the random characters and its @gmail.com account. Geek Squad will never email from a Gmail account. Another thing about the email address you need to watch for is misspelled or changes in the spelling of the domain. An example is for @facebook.com I have seen cybercriminals purchase domains like @faceb00k.com notice the O are zeros instead of letters.
Now the body of the email- Notice the broken English on the highlighted area. Most of these come from overseas and English is not their first language. I strongly suggest watching for miss spelled words, bad grammar, and broken English.
Lastly, notice how the phone number is formatted. In the US we format our phone numbers Country code, Area Code, Central office, and or location code then the line number. An example of this format is 1-701-837-6202.
Several phishing emails include a link lets look at a phishing email with a link.
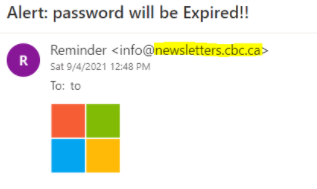
One of the most common phishing emails we see in the business world is for Microsoft Office 365. Let’s look at a real phishing email to mimic an Office 365 email.
Just like the example above, notice the sending email address is not from Microsoft.com. With Microsoft, you will need to watch for generic email addresses. An example of a Microsoft generic email address is: TEST@MagicCitySystem.onmicrosoft.com. If you receive any emails from an onmicrosoft.com account chances, are they are phishing emails.
Never click the link from a possible phishing scam/attack! Once you click the link you could be compromised! Just hover your mouse over the link without clicking on it.
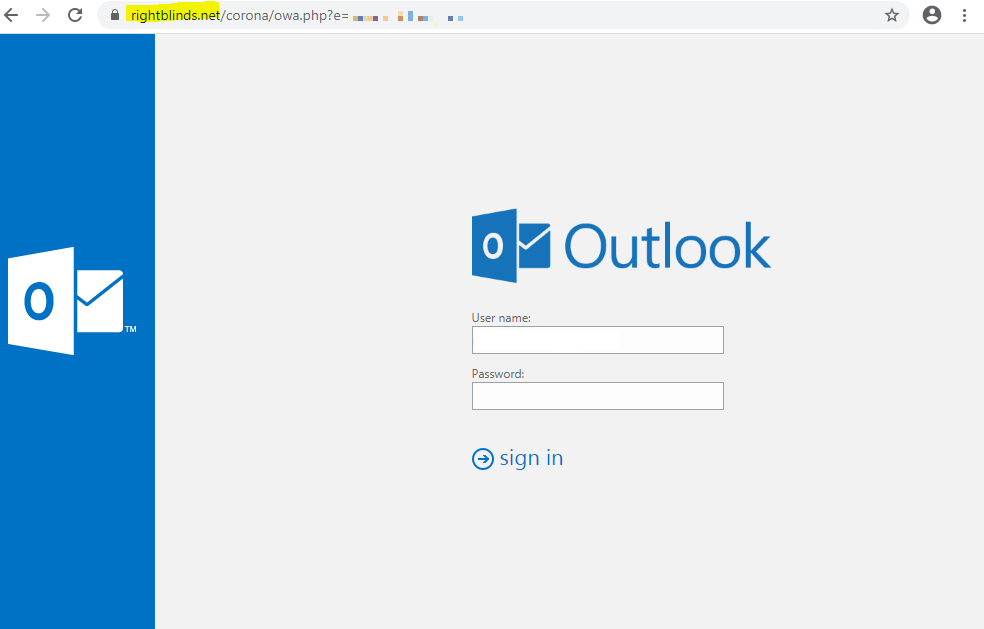
When you hover the mouse over the link, it will show you the URL that the link is taking you to. In Outlook it will show right next to the link, but if you are using webmail it will show in the bottom right corner. We highlighted the link in the two images to the right. Notice the link says https://naturalterapia.eu/ and NOT https://Microsoft.com?
Let’s say you do accidentally click on the link; it could download a program to compromise your computer. In other instances, clicking the link will take you to a fake Microsoft page to steal your credentials. Hackers will also send an email to all of your contacts, from you, in hopes that they will click on the link and enter their information as well. The goal of this is to collect as many email addresses as possible to sell. This isn’t just a pain; it could also damage the company’s reputation along with financial losses.
This is an example of what the login page might look like. Hackers can make this look very real, but did you notice the URL/ Address is not https://Microsoft.com?
Even if you receive an email from a contact that you work with verify the link before you click it. If it doesn’t match the company or is random don’t click it and call the person that sent the email to verify they actually sent the email.
Magic City Systems Inc. Offers all kinds of training options give us a call for more information at 701-837-6202 or fill out the form below.
If your business would like a Free Month of training please fill out the form below.